Best in class security protocols

Data Integrity

ISO Certified











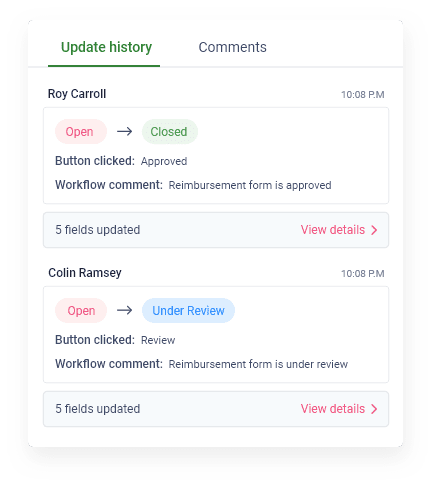

Secure Shell or Secure Socket Shell, is a network protocol that gives users, particularly system administrators, a secure way to access a computer over an unsecured network.

In cryptography, key size refers to the number of bits in a key used by a cryptographic algorithm which defines the upper-bound on an algorithm\'s security. user productivity in their preferred language With in-built language translations

HTTPS only access ensures the integrity and confidentiality of data between the user\'s computer and the site

IP Restrictions allow administrators or organization owners to limit access of their business data to only a specified and registered IP addresses range.

Simply put security architecture for data at rest is similar to a secured vault while data in motion is protected like an armored car.